Phishing link is used to trick people into visiting websites that are under the control of cybercriminals and are set up to steal sensitive information or install malware on the victim’s computer.
Understanding phishing
What is a phishing attack?
A phishing attack is a type of cybercrime where cyber criminals try to trick people into giving away sensitive information, such as passwords, credit card numbers and other confidential data. Phishing is also used to trick users to install malware to their computers.
They often do this by sending a phishing email or messages that appear to come from a trusted source, like a bank or a popular service provider. Usually in those messages victim is tricked to click on a phishing link or open malicious files.
Nowadays, the number of phishing emails is steadily increasing. According to the Zscaler ThreatLabz 2024 Phishing Report, researchers noted a nearly 60% global increase in phishing attacks in 2023 compared to the previous year.
Phishing mails are becoming more personalized, so even more attention must be paid to ways to recognise phishing emails.
An important aspect of recognizing phishing emails is the ability to understand where the links in the email lead. In this article, we will thoroughly examine the patterns cybercriminals use to create seemingly credible links.
Impact of phishing attacks
Phishing attacks have a significant impact on both individuals and businesses. Beyond financial loss, these attacks erode trust in online services and can lead to long-lasting emotional distress. Identity theft is also a potential consequence of phishing attacks.
Research from Egress’s 2024 email security report reveals that almost 80% of account takeover incidents originated from phishing emails.
Understanding links and its structure
Before we can discuss the deception methods used by criminals in phishing links, let’s provide an overview of what links and URL consist of. This knowledge makes it also easier to recognise malicious links.
Understanding link structure helps in identifying a malicious link, which is often used in URL phishing attacks to direct users to phishing pages designed to harvest sensitive information or distribute malware.
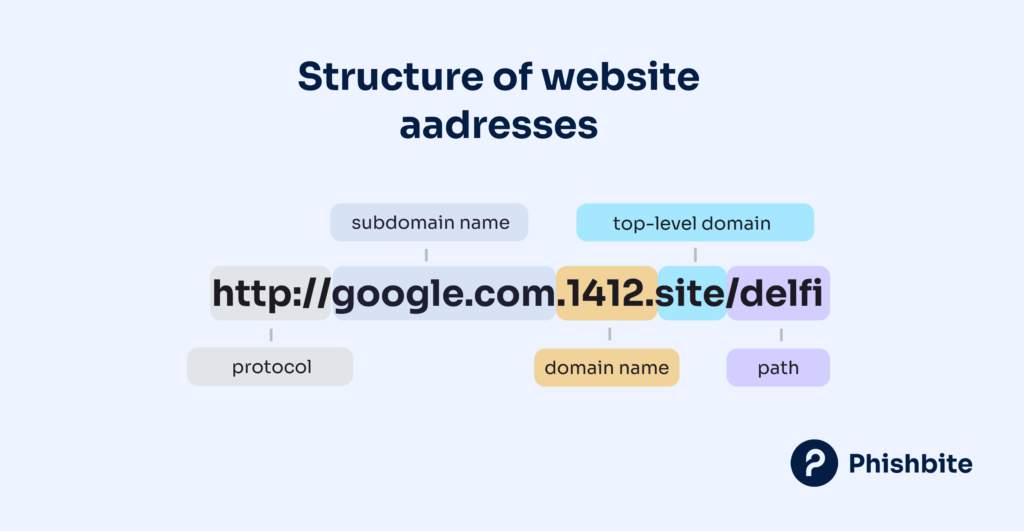
Protocol
The protocol indicates the method used to fetch the resource from the server.
Common protocols include:
- http:// (HyperText Transfer Protocol): Unencrypted communication protocol. Mostly, it is not used on websites because browsers display a warning to users when opening the URL using http protocol.
- https:// (HyperText Transfer Protocol Secure): Data between web server and customer computer is encrypted.
Subdomain(s)
A subdomain is a subdivision of the main domain and can be used to organize and separate different sections of a website. It is important to know that companies may use a variety of names in subdomain names, including the names of other brands. Cybercriminals also use this to create phishing URLs that are containing original brand name.
For example:
- blog.example.com
- new.shop.example.com
In these examples, “blog” and “new.shop” are subdomains of the main domain “example.com“
Domain Name
The domain name is the human-readable address of a website, typically representing the brand or the name of the website. A domain name is always registered under a company’s name and is associated with that company’s brand. If someone registers a brand related to another trademark, the trademark owner can file a dispute and request the right to obtain the domain.
For example:
- phishbite in phishbite.com
Domain name together with Top-Level Domain it the primary identifier of the website.
Top-Level Domain (TLD)
The TLD is the last segment of the domain name, following the final dot.
Common TLDs include:
- .com (commercial)
- .edu (education)
- .ee, .eu, .de, .it, .pt … (country and region based TDL’s)
As of 2024, there are 1,589 top-level domains. This means that companies cannot register their brand under all top-level domains, and this creates an opportunity for cybercriminals to use available TLD domains in the brand’s name.
For example, in www.example.com, .com is the TLD.
Path
Path also known as sub-page, specifies a particular page or resource within the website. It follows the domain and TLD. It is possible to put anything in the domain path; it can include the names of other brands, etc.
For example:
- /about in www.example.com/about
- /products/item1 in www.example.com/products/item1
The path directs users to a specific page within the site.
11 commonly used phishing link patterns
Phishing websites often have URLs like legitimate websites but with slight variations.
Here is an overview of the typical patterns that cyber criminals use for phishing links in scam emails.
Embedding misleading URL in phishing link text
This is the most common deception method and it’s often combined with other malicious URL hiding methods.
Misleading URLs often lead to a phishing site. It is important to understand that the address appearing as a link in the email text is just text, and the actual link may lead somewhere else entirely. You should never trust the information that appears as link text. The actual link address can be seen by hovering over the link to see where it really points.
- Example: Click here for a prize links to phishingsite.com
Using lookalike letters in phishing link
This malicious URL hiding method uses letters and symbols that look very similar to the original URL but are different. Typical examples include using a capital “I” in place of a lowercase “l” and substituting “m” and “n” for each other.
Examples:
- paypa1.com (using 1 instead of l)
- WaImart.com (using a capital “i” instead of a lower case “l”)
- Delivery.ips.com (adding “delivery” to the URL in hopes that you won’t notice they’ve spelled “UPS” as “IPS”)
- microsöft.com (using ö instead of o)
Using misspelled phishing link
This method used in phishing attacks is quite like the previous one. It involves creating a typographical error in the domain name that may go unnoticed.
Examples:
- goggle.com instead of google.com (one o is replaced with g)
- BankoffAmerica.com (adding an extra “f”)
Using hyphenated in phishing link
Every number and symbol in a website’s domain name matters. Adding even one can create a different domain that someone else might own. The same goes for hyphens in malicious links. The address may look similar but isn’t the same, giving criminals the chance to register it.
Example:
- pay-pal.com instead of paypal.com
Adding legitimate-looking subdomains to phishing link
If a company owns a domain, they can add unlimited subdomains with any names. This allows phishing links to use the company’s name. The similarities between the two addresses create the impression of a secure link, making the recipient less aware of the ongoing attack.
Example:
- myuniversity.edurenewal.com (instead of myuniversity.edu/renewal)
Adding legitimate-looking parameters or subdomains
For example, myuniversity.edu/renewal URL is changed to myuniversity.edurenewal.com. Similarities between the two addresses offer the impression of a secure link, making the recipient less aware that an attack is taking place.
Examples:
- https://malicious.com/login?source=facebook.com
- https://3344322.com/p=paypal.com
Using IP Addresses Instead of Domain Names
Every web server has an IP address in addition to its domain, and websites can be accessed directly using this IP address. Using an IP address can confuse regular users, who might think it’s normal.
Never click on links that don’t show a domain name because you can’t be sure who owns the website or if it’s trustworthy.
Example:
- http://192.168.1.1/login
Using URL shorteners in phishing links
Cybercriminals use URL shorteners to hide the true destination of a link, making phishing emails more convincing. These shortened links look harmless and can trick people into clicking on them.
Once clicked, users are redirected to fake websites designed to steal their information.
Examples:
- https://bit.ly/3xYzZ8u
- https://tinyurl.com/swedbanklogin
Using redirects via official sites
Phishing attackers often exploit redirects through official sites to make their malicious links appear more legitimate. By embedding their phishing URLs within the redirect parameters of trusted websites, they can deceive users into believing they are clicking on a safe link. This technique leverages the credibility of the official site to mask the true destination, increasing the chances of successful phishing attacks
Example:
- https://www.google.com/url?q=http://malicious.com
Creating Subtle Variations in TLDs
There are many top-level domains for web addresses (like .com, .eu, .net, .biz, .ee, and so on for each country). Often, brands don’t register their company domains on all these top-level domains.
This gives cyber criminals a chance to take the unused domains and make phishing links look like the company’s official web address.
Example:
- example.net instead of example.com
Utilizing Punycode to Mimic Legitimate URL
These Punycode representations use characters from different alphabets that look very similar to the original characters, making it difficult for users to detect the fraud. Often Punycode-based URLs can bypass traditional security filters and fool even vigilant users into thinking they are accessing a genuine website.
Examples:
- xn--pple-43d.com (where the “a” in apple is replaced with a Cyrillic “а” of www.apple.com)
- xn--micrsoft-w5e.com (where the “o” in microsoft is replaced with a Cyrillic “о”)
Identifying Phishing Links
How to spot suspicious URLs and phishing links
Always verify the actual website address before clicking on a link. The easiest way to do this is to hover your mouse over the link, and the email client will display the real address. Be careful when checking the name; make sure the link does not use the deceptive methods.
If you are unsure whether the link is trustworthy, do not click on it. If in doubt, use a search engine (such as Google) to look up the company’s name and visit their official website to find the referenced information.
Red flags in email messages
- Be always cautious when clicking on links in emails, especially from unknown senders.
- Be wary of emails that ask for sensitive information, such as passwords or credit card numbers.
- Look for spelling and grammar mistakes in the email.
- Be cautious of generic greetings, such as “Dear customer” instead of your actual name.
- Phishing emails often ask for personal or financial information, such as usernames, passwords, credit card numbers, or bank account details.
Protecting Yourself
Use security software
Use antivirus and email protection software and set it to update automatically. Security software helps protect against phishing emails by detecting and blocking malicious messages. It scans emails for suspicious links and attachments. Types of security software include antivirus programs, email filters, and anti-phishing tools.
Such software catches many phishing and scam emails, but they are not 100% effective, so it is necessary to combine them with other protection methods.
Provide security awareness training and phishing simulations
Phishing training helps people recognize and deal with fake messages.
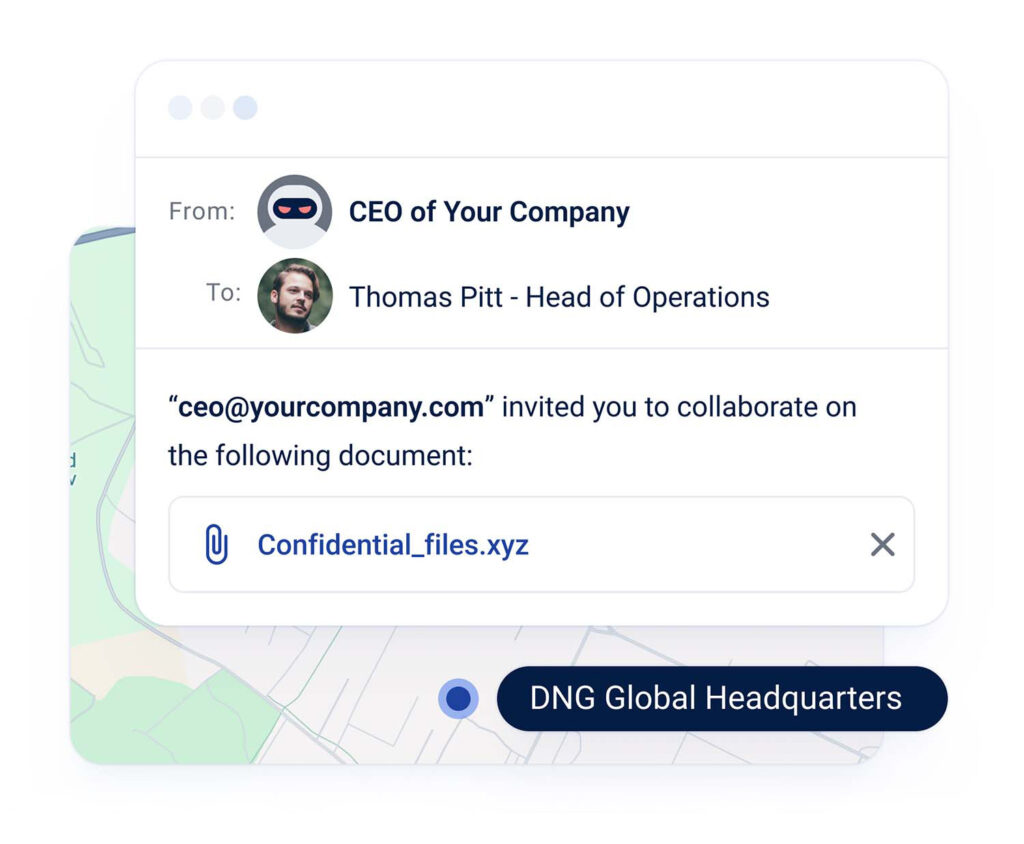
Training is effective when it includes practical phishing tests, meaning that during training, users are sent phishing simulation emails. If the user makes a mistake, the employee is trained on how they should have recognized the phishing email. This approach, on one hand, increases employees’ security awareness. On the other hand, it provides the company with the necessary transparency to understand the extent of their phishing risks and which employees need additional training.
Phishbite is a phishing simulation and training environment that is easy to implement and operates automatically by sending personalized phishing test emails based on the company and employee profile.
Conclusion
Phishing is one of the most impactful sources of cyberattacks, and protecting against it is crucial for mitigating a company’s cybersecurity risks. It is important for employees to be aware and able to recognize phishing emails and the fraudulent links they contain.
Be aware and careful about what you click on.




